Multi-tenancy architecture is a system design where a single instance of software serves multiple customers, known as tenants. Each tenant's data is isolated and invisible to others, ensuring privacy and security. This approach is efficient because it allows resource sharing, reduces costs, and simplifies updates. Tenants can customize their experience without affecting others. Multi-tenancy is commonly used in cloud services, where different users or organizations share the same infrastructure but operate independently
What is Multi-Tenancy Architecture?
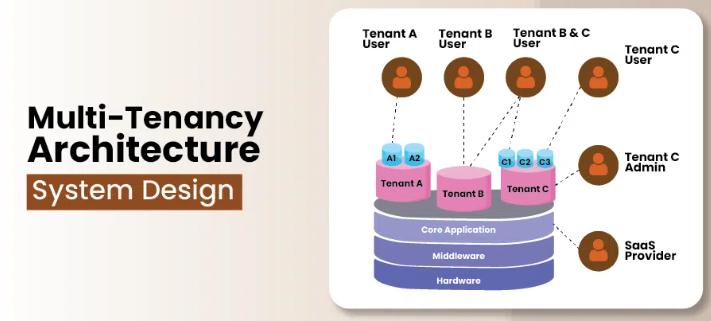
Multi-tenancy architecture in system design, as illustrated in the provided image, involves a layered framework where multiple tenants (Tenant A, Tenant B, Tenant C) share a single instance of the core application, middleware, and hardware infrastructure. Each tenant operates independently, with their own distinct users and data sets.
For instance:
Tenant A has users A1 and A2, Tenant B has a single user, and Tenant C has multiple users (C1, C2, C3) along with an admin. This architecture allows these tenants to coexist on the same system while maintaining strict data isolation, ensuring that the data and actions of one tenant do not affect others.
The SaaS (Software as a Service) provider manages the underlying hardware and software layers, providing scalability, maintenance, and updates across all tenants simultaneously.
- This setup enhances resource utilization efficiency, reduces operational costs, and enables each tenant to customize their user experience without compromising the integrity or performance of the shared system.
- The design ensures that the tenants benefit from the shared infrastructure while enjoying the privacy and security of their data and operations.
Types of Multi-Tenancy Architectures
Multi-tenancy architectures in system design are varied, each offering distinct ways to manage multiple tenants while balancing factors like resource sharing, isolation, and complexity. The primary types include:
1. Isolated Tenancy
Each tenant has their own separate instance of the application and database. This approach provides the highest level of isolation and security, making it ideal for applications requiring strict data segregation and compliance with stringent regulations.
- Superior data isolation and security, straightforward compliance with regulatory requirements.
- High operational costs due to redundant resource allocation, less efficient use of resources, and challenges in scalability and maintenance.
2. Shared Application with Separate Databases
Multiple tenants share the same application instance, but each has a separate database. This model strikes a balance between resource utilization and data isolation, offering efficient use of application resources while maintaining tenant-specific databases.
- Better resource utilization compared to isolated tenancy, maintained data isolation at the database level, simpler application management.
- Increased complexity in managing multiple databases, potential challenges in scaling the database layer independently.
3. Shared Application and Shared Database with Separate Schemas
Tenants share the same database, but each tenant's data is stored in a separate schema. This method provides efficient database resource use while maintaining some level of data segregation.
- Efficient database resource utilization, simplified application deployment and management, reasonable data isolation.
- Less isolation compared to separate databases, potential for schema conflicts, increased complexity in schema management and migration.
4. Shared Everything
Tenants share the same application instance and the same database tables. This model maximizes resource utilization and simplifies deployment and scaling, as all tenants operate within the same environment.
- Maximum resource utilization, simplified deployment and scaling processes, lower operational costs.
- Complex data management to ensure tenant data isolation, higher risk of data leakage and security concerns, potential performance bottlenecks if tenant activity is not well managed.
5. Hybrid Multi-Tenancy
Combines elements from different multi-tenancy models to balance resource efficiency and data isolation based on specific needs. This approach allows flexibility in choosing the best aspects of each model to optimize performance and cost.
- Highly adaptable and flexible, can be tailored to meet specific requirements of isolation, performance, and cost-efficiency.
- Increased complexity in implementation and management, potential trade-offs between isolation and resource utilization need to be carefully managed.
Design Principles of Multi-Tenancy
Designing a multi-tenant system involves adhering to specific principles to ensure scalability, security, maintainability, and efficiency. Here are key design principles for multi-tenancy in system design:
- Data Isolation:
- Separation of Tenant Data: Ensure that each tenant's data is securely isolated from others, either through separate databases, schemas, or logical data partitions.
- Access Control: Implement strict access controls to prevent unauthorized access to tenant data. Use role-based access control (RBAC) and tenant-specific permissions.
- Scalability:
- Elasticity: Design the system to scale horizontally and vertically to handle an increasing number of tenants and users. This includes auto-scaling capabilities for both application and database layers.
- Resource Allocation: Allocate resources dynamically based on tenant demand to optimize performance and cost. Use containerization or virtualization to manage resources efficiently.
- Performance Isolation:
- Resource Limits: Implement mechanisms to prevent one tenant's heavy usage from affecting the performance of others. Use quotas, throttling, and resource limits to ensure fair resource distribution.
- Load Balancing: Distribute workloads evenly across servers and services to prevent bottlenecks and ensure consistent performance.
- Security:
- Data Encryption: Encrypt tenant data both at rest and in transit to protect against unauthorized access and breaches.
- Security Monitoring: Continuously monitor and audit tenant activity for security anomalies and potential threats.
- Tenant Customization:
- Configuration Options: Allow tenants to customize their environment, such as user interfaces, workflows, and business rules, without affecting other tenants.
- Extensibility: Provide APIs and extension points for tenants to integrate their specific requirements and third-party services.
- Operational Efficiency:
- Centralized Management: Implement centralized monitoring, logging, and management tools to oversee the entire multi-tenant environment efficiently.
- Automated Provisioning: Automate the provisioning and deprovisioning of tenant environments to reduce operational overhead and ensure consistency.
- Cost Efficiency:
- Resource Sharing: Maximize resource sharing while maintaining isolation to reduce overall costs. Optimize infrastructure usage through multi-tenancy to lower expenses.
- Billing and Metering: Implement precise billing and metering systems to accurately charge tenants based on their resource usage..
Core Components of Multi-Tenant Systems
Designing a multi-tenant system involves integrating several core components to ensure effective resource sharing, data isolation, scalability, and security. Here are the core components of multi-tenant systems:
1. Tenant Management:
- Tenant Provisioning: Automates the creation and configuration of tenant environments. This includes setting up databases, allocating resources, and initializing tenant-specific configurations.
- Tenant Isolation: Ensures data and configuration isolation between tenants. Techniques include using separate databases, schemas, or logical partitions.
- Tenant Metadata: Stores metadata about each tenant, including configuration settings, resource allocations, and usage statistics.
2. Authentication and Authorization:
- Identity Management: Manages user identities and authentication across tenants. Supports Single Sign-On (SSO) and integration with external identity providers.
- Access Control: Implements role-based access control (RBAC) to manage user permissions within and across tenants, ensuring users have appropriate access to resources.
3. Data Management:
- Data Isolation: Ensures each tenant's data is stored separately and securely, using techniques like separate databases, schemas, or row-level security.
- Data Encryption: Encrypts data at rest and in transit to protect tenant data from unauthorized access and breaches.
- Backup and Recovery: Implements robust backup and recovery mechanisms to protect tenant data and ensure business continuity.
4. Scalability and Performance:
- Load Balancing: Distributes incoming requests evenly across servers to optimize resource utilization and ensure high availability.
- Auto-Scaling: Automatically adjusts the number of resources (servers, databases, etc.) based on current demand to maintain performance and cost-efficiency.
- Resource Management: Monitors and allocates resources dynamically to prevent resource contention and ensure fair usage across tenants.
5. Security and Compliance:
- Security Monitoring: Continuously monitors for security threats and anomalies, implementing intrusion detection and prevention systems.
- Compliance Management: Ensures the system meets regulatory requirements such as GDPR, HIPAA, and PCI DSS. Includes maintaining audit logs and data governance policies.
6. Customization and Extensibility:
- Configuration Management: Allows tenants to customize their environment, including UI customization, workflow configurations, and business rules.
- APIs and Extensions: Provides APIs and extension points for tenants to integrate their own tools and services, enabling extensibility without affecting other tenants.
7. Operational Efficiency:
- Monitoring and Logging: Implements centralized monitoring and logging to track system performance, tenant activities, and errors.
- Automation: Automates routine tasks like provisioning, scaling, updates, and maintenance to reduce operational overhead and ensure consistency.
- Multi-Tenant Dashboard: Provides an admin interface for managing tenants, monitoring usage, and configuring system settings.
Performance Optimizations in Multi-Tenancy Architecture
Performance optimization in a multi-tenancy architecture is crucial to ensure that the system can efficiently handle multiple tenants without compromising on speed, reliability, or user experience. Here are several key strategies for optimizing performance in a multi-tenant system:
- Resource Management:
- Dynamic Resource Allocation: Allocate resources dynamically based on tenant demand. Implement auto-scaling mechanisms to adjust compute resources (CPU, memory) as needed.
- Resource Quotas: Set resource quotas to prevent any single tenant from monopolizing shared resources, ensuring fair resource distribution.
- Caching Strategies:
- Tenant-Specific Caches: Use separate caches for each tenant to isolate their data and reduce the risk of cache pollution.
- Distributed Caching: Implement distributed caching systems like Redis or Memcached to store frequently accessed data closer to the application, reducing database load.
- Load Balancing:
- Even Traffic Distribution: Use load balancers to distribute incoming traffic evenly across multiple instances of the application, preventing any single instance from becoming a bottleneck.
- Geographical Load Balancing: Distribute traffic based on geographical location to reduce latency and improve response times for users in different regions.
- Database Optimization:
- Indexing: Ensure that database indexes are properly configured to speed up query performance, especially for common queries.
- Sharding: Implement database sharding to distribute data across multiple servers, allowing the system to scale horizontally and handle more requests.
- Connection Pooling: Use connection pooling to manage database connections efficiently, reducing the overhead of establishing connections repeatedly.
- Efficient Query Design:
- Optimized Queries: Write efficient SQL queries to minimize execution time. Avoid complex joins and unnecessary data retrieval.
- Read Replicas: Use read replicas to offload read-heavy traffic from the primary database, improving performance for read operations.
- Application-Level Optimization:
- Asynchronous Processing: Implement asynchronous processing for non-critical tasks to free up resources for more important operations.
- Microservices Architecture: Use a microservices architecture to break down the application into smaller, manageable services that can be independently scaled and optimized.
Challenges in Multi-Tenancy Architecture
Multi-tenancy is a design architecture where a single instance of a software application serves multiple tenants (organizations or users). While it offers benefits like cost savings and efficient resource utilization, it also presents several challenges:
- Data Security and Isolation: Ensuring that data from one tenant is securely isolated from others is critical. A breach or data leak can have serious consequences. Techniques like encryption, access controls, and tenant-specific data partitions help address these issues.
- Performance and Scalability: Managing performance for multiple tenants can be challenging. One tenant's heavy usage might affect others. Implementing efficient resource allocation, load balancing, and monitoring is crucial.
- Customization and Configuration: Different tenants may have different needs and preferences. Providing customization options while maintaining a single codebase requires a flexible architecture and careful management of configuration settings.
- Maintenance and Upgrades: Rolling out updates or patches can be complex. Changes must be tested thoroughly to ensure they don't disrupt any tenant's operations. Strategies for minimizing downtime and ensuring smooth transitions are essential.
- Compliance and Regulations: Different tenants might be subject to different regulatory requirements. The system must accommodate these varying compliance needs without compromising security or functionality.
- Resource Allocation: Efficiently managing and allocating resources among tenants to prevent any single tenant from monopolizing resources is a challenge. Dynamic resource management and monitoring can help.
Benefits of Multi-Tenancy Architecture
Multi-tenancy architecture offers several benefits, making it an attractive option for many organizations:
- Cost Efficiency: By sharing a single instance of the software and infrastructure among multiple tenants, organizations can significantly reduce costs related to hardware, maintenance, and support.
- Resource Optimization: Multi-tenancy allows for efficient use of resources. It maximizes server utilization and reduces redundancy, leading to better performance and scalability.
- Simplified Maintenance: Updates, patches, and upgrades are performed once for the entire system, rather than for each tenant individually. This simplifies maintenance and ensures all tenants benefit from the latest features and security enhancements simultaneously.
- Scalability: The architecture can easily scale to accommodate a growing number of tenants without requiring major changes to the infrastructure. This flexibility allows the system to handle increased loads and adapt to varying demands.
- Rapid Deployment: New tenants can be onboarded quickly and efficiently, as the system already exists and only requires configuration adjustments rather than a complete setup.
- Consistency: All tenants use the same version of the application, ensuring consistency in features and functionality. This standardization can simplify support and troubleshooting.
- Centralized Management: Admins can manage and monitor all tenants from a single interface, making it easier to oversee operations, track performance, and enforce policies.
Real World Examples of Multi-Tenancy Architecture
Here are some real-world examples of multi-tenancy architecture across various industries and applications:
1. Cloud Services (e.g., AWS, Azure, Google Cloud)
- Amazon Web Services (AWS): AWS uses multi-tenancy to offer a variety of services to different customers from the same physical infrastructure. For example, Amazon EC2 instances and Amazon S3 storage are shared among multiple tenants, with strict isolation and security measures in place.
- Microsoft Azure: Azure provides multi-tenant cloud services for computing, storage, and databases, allowing different organizations to use the same underlying infrastructure while maintaining data separation and security.
2. Software-as-a-Service (SaaS) Applications
- Salesforce: Salesforce is a leading CRM platform that uses multi-tenancy to serve multiple organizations from a single application instance. Each organization's data is securely isolated, and the platform supports extensive customization for individual tenants.
- Slack: Slack uses multi-tenancy to provide messaging and collaboration services to numerous companies and teams. Each tenant (company) has its own workspace with isolated data and user management.
3. Email Hosting Providers
- Gmail: Google's Gmail service uses multi-tenancy to handle millions of users with separate mailboxes and settings while operating on shared infrastructure.
- Microsoft 365 (Outlook): Microsoft 365 provides email and other productivity tools to multiple organizations from a single platform, ensuring data isolation and security.
Conclusion
In conclusion, multi-tenancy architecture is a powerful design strategy that allows a single software instance to serve multiple clients while keeping their data and settings separate. It offers significant benefits, including cost savings, efficient resource use, and simplified maintenance. However, it also presents challenges such as ensuring data security, managing performance, and handling customization. By addressing these challenges with thoughtful design and technology, organizations can leverage multi-tenancy to deliver scalable, cost-effective, and reliable solutions across various industries.
Source: Internet Collection - The Base.